Strategic Guide for Enterprises
Installation Options
KanBo is an integrated platform that addresses all aspects of work coordination. It serves as an ideal software solution that acts as a liaison between company strategy and daily operations. Whether your team operates remotely, onsite, or in a hybrid model, KanBo offers flexible installation options that provide control over your work environment while adhering to the highest security standards.

Cloud Installation
Suited for those who prioritize agility and convenience with scalable solutions.

GCC High Cloud Installation
Designed for regulated industries needing compliance with federal standards.

On-premises Installation
Ideal for organizations requiring complete control over their data and infrastructure.

Hybrid Installation
Combines the benefits of on-premises and cloud installations for maximum flexibility and security.
Understanding KanBo’s Installation Options
Scalability & Flexibility
KanBo scales efficiently to support 1,000+ daily users, adapting to growing enterprise needs with flexible resource allocation and performance optimization.
Compliance
Meets industry regulations and security standards across all deployment options, with specialized compliance for government (GCC High) and enterprise requirements.
Integration
Seamless connectivity with Microsoft ecosystem (Teams, SharePoint, Microsoft 365) and existing enterprise systems through standardized APIs and protocols.
Data Ownership
Full control over data location, storage, and access policies. Choose between on-premises, cloud, or hybrid storage to meet sovereignty requirements.
Resource Planning
Optimize IT resource allocation with flexible deployment options. Scale computing resources, storage, and user licenses based on organizational needs.
Customization
Adapt KanBo to specific organizational workflows with configurable interfaces, custom processes, and integration options across all deployment types.
Strategic Guide for Enterprises
Installation Options
KanBo is an integrated platform that addresses all aspects of work coordination. It serves as an ideal software solution that acts as a liaison between company strategy and daily operations. Whether your team operates remotely, onsite, or in a hybrid model, KanBo offers flexible installation options that provide control over your work environment while adhering to the highest security standards.

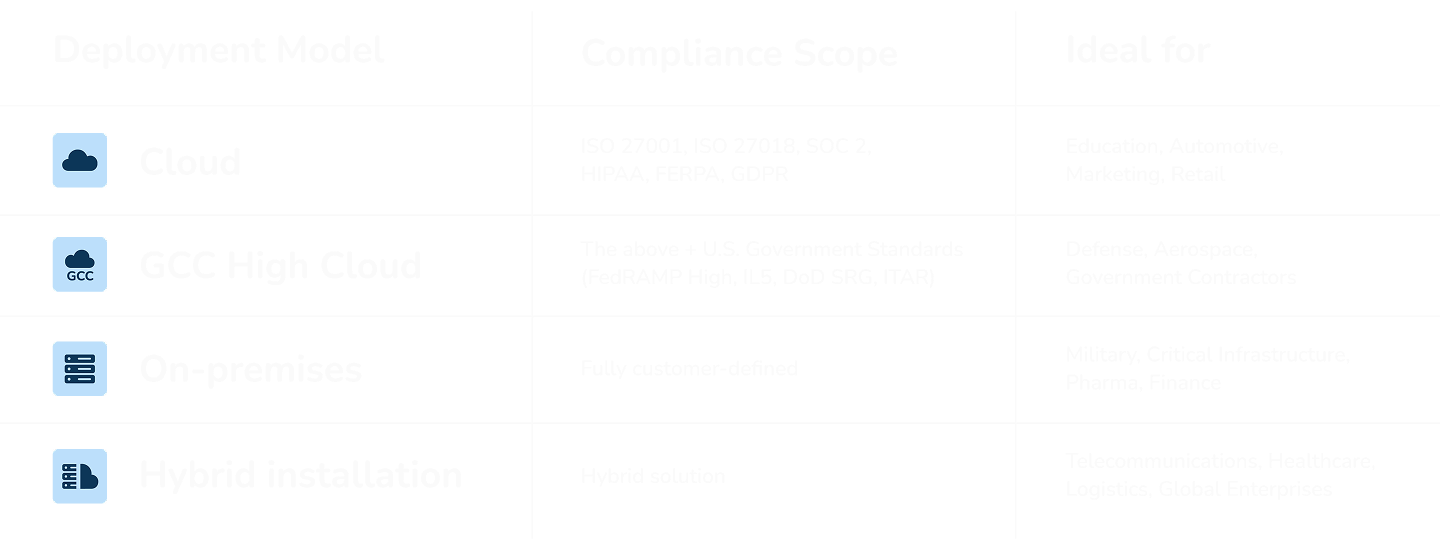
Cloud Installation
Suited for those who prioritize agility and convenience with scalable solutions.

GCC High Cloud Installation
Designed for regulated industries needing compliance with federal standards.

On-premises Installation
Ideal for organizations requiring complete control over their data and infrastructure.

Hybrid Installation
Combines the benefits of on-premises and cloud installations for maximum flexibility and security.
Understanding KanBo’s Installation Options
Scalability & Flexibility
KanBo scales efficiently to support 1,000+ daily users, adapting to growing enterprise needs with flexible resource allocation and performance optimization.
Compliance
Meets industry regulations and security standards across all deployment options, with specialized compliance for government (GCC High) and enterprise requirements.
Integration
Seamless connectivity with Microsoft ecosystem (Teams, SharePoint, Microsoft 365) and existing enterprise systems through standardized APIs and protocols.
Data Ownership
Full control over data location, storage, and access policies. Choose between on-premises, cloud, or hybrid storage to meet sovereignty requirements.
Resource Planning
Optimize IT resource allocation with flexible deployment options. Scale computing resources, storage, and user licenses based on organizational needs.
Customization
Adapt KanBo to specific organizational workflows with configurable interfaces, custom processes, and integration options across all deployment types.

Strategic Guide for Enterprises
Installation Options
KanBo is an integrated platform that addresses all aspects of work coordination. It serves as an ideal software solution that acts as a liaison between company strategy and daily operations. Whether your team operates remotely, onsite, or in a hybrid model, KanBo offers flexible installation options that provide control over your work environment while adhering to the highest security standards.
Understanding KanBo’s Installation Options
Scalability & Flexibility
KanBo scales efficiently to support 1,000+ daily users, adapting to growing enterprise needs with flexible resource allocation and performance optimization.
Compliance
Meets industry regulations and security standards across all deployment options, with specialized compliance for government (GCC High) and enterprise requirements.
Integration
Seamless connectivity with Microsoft ecosystem (Teams, SharePoint, Microsoft 365) and existing enterprise systems through standardized APIs and protocols.
Data Ownership
Full control over data location, storage, and access policies. Choose between on-premises, cloud, or hybrid storage to meet sovereignty requirements.
Resource Planning
Optimize IT resource allocation with flexible deployment options. Scale computing resources, storage, and user licenses based on organizational needs.
Customization
Adapt KanBo to specific organizational workflows with configurable interfaces, custom processes, and integration options across all deployment types.

Cloud Installation
Suited for those who prioritize agility and convenience with scalable solutions.

GCC High Cloud Installation
Designed for regulated industries needing compliance with federal standards.

On-premises Installation
Ideal for organizations requiring complete control over their data and infrastructure.

Hybrid Installation
Combines the benefits of on-premises and cloud installations for maximum flexibility and security.
Strategic Guide for Enterprises
Installation Options
KanBo is an integrated platform that addresses all aspects of work coordination. It serves as an ideal software solution that acts as a liaison between company strategy and daily operations. Whether your team operates remotely, onsite, or in a hybrid model, KanBo offers flexible installation options that provide control over your work environment while adhering to the highest security standards.

Cloud Installation
Suited for those who prioritize agility and convenience with scalable solutions.

GCC High Cloud Installation
Designed for regulated industries needing compliance with federal standards.

On-premises Installation
Ideal for organizations requiring complete control over their data and infrastructure.

Hybrid Installation
Combines the benefits of on-premises and cloud installations for maximum flexibility and security.

Cloud Installation
Complience
The KanBo cloud is based on Microsoft 365, which maintains compliance with security standards such as ISO 27001, ISO 27018, SOC 2, HIPAA, FERPA, and GDPR.






Microsoft Entra ID
With Microsoft Entra ID (Active Directory) authentication, you can access KanBo and Microsoft applications with a single sign-on. You can also set up multi-factor authentication to provide additional security.
Access from any location
Cloud installation enables easy scalability and the ability to access KanBo from anywhere, making it a great choice for organizations that prioritize agility and convenience.
Documents Integration
Using Microsoft 365 services allows you to seamlessly integrate data with other applications. There is no need to download documents to your device. Your data is encrypted both in transit and at rest.
Multi-Factor Authentication
With Microsoft Entra ID, you can set up multi-factor authentication, such as a fingerprint scan. This feature protects your personal data from unauthorized third parties.
Microsoft Teams Integration
KanBo is closely integrated with Teams. This allows you to send notifications from KanBo to Teams users and preview what’s happening in KanBo from within Teams.
How will cloud deployment align with your digital transformation strategy?
Ensures KanBo implementation supports broader organizational goals and cloud migration initiatives.
What’s your organization’s stance on cloud security and data handling?
Defines necessary security controls and data protection measures in cloud environment.
How will this integrate with your existing cloud services?
Impacts architecture decisions and integration approach with current cloud infrastructure.

GCC High Cloud Installation
Government Compliance
Meet the Department of Defense’s (DOD) strict security requirements with Microsoft 365 GCC High integration. Adherence to FedRAMP High, IL5, DoD SRG, and ITAR.



Isolated Environment
Raise your cybersecurity level by operating in a dedicated government cloud infrastructure with enhanced security controls.
Specialized Security
Implement DOD-specific security protocols and monitoring systems to ensure the security of sensitive data.
Endpoint Configuration
Set up proper government cloud endpoints following DOD security guidelines.
Access Control
Implement proper CAC/PIV authentication methods for secure access.
Security Monitoring
Configure SIEM integration following government security requirements.
What security clearance levels need to be supported?
Determines access control requirements and security implementation specifics.
How will this align with your current government compliance framework?
Ensures KanBo deployment meets existing compliance requirements and security standards.
What are your specific DOD security requirements?
Defines necessary security controls and certifications for implementation.

On-Premises Installation
Infrastructure Control
Leverage existing data centers and security systems while maintaining complete oversight of data flows and processing.
SharePoint Integration
Direct connection to your SharePoint farm enables seamless document management and user authentication.
Security Framework
Implement custom security policies that align with your organization’s specific compliance requirements. Keep your finger on the pulse.
Active Directory Setup
Ensure User Profile Service is properly configured with AD sync before starting KanBo deployment.
Security Planning
Implement proper SSL certificates and firewall rules based on your network architecture.
Performance Optimization
Configure SQL Server resources based on expected user load and data volume.
What level of infrastructure control does your organization require?
Understanding your control requirements shapes how KanBo integrates with existing security frameworks and compliance policies.
How does your current security framework handle external applications?
Your security approach to external systems directly impacts implementation strategy and required security measures.
What’s your organization’s approach to data sovereignty?
Data location and processing requirements determine technical architecture and compliance measures.

Hybrid Installation
Deployment Flexibility
Balanced distribution of workloads between on-premises and cloud-based systems, taking into account the specific security requirements of each environment.
Migration Control
Move components to the cloud gradually while maintaining the highest security standards.
Resource Optimization
Leverage existing infrastructure while capitalizing on the scalability of cloud computing.
Connectivity Setup
Establish secure connections between on-premises and cloud environments
Security Boundaries
Define clear security zones and data flow policies across environments.
Authentication Chain
Configure unified authentication across the hybrid infrastructure.
Which workloads in your organization require specific deployment locations?
Determines optimal distribution of KanBo components between cloud and on-premises.
How does your security policy handle cross-environment data flow?
Shapes security architecture and data protection measures across environments.
What’s your long-term infrastructure evolution strategy?
Ensures KanBo deployment aligns with future infrastructure plans and scalability needs.
Make the
Right
Choice
Security Requirements
Assess how critical data protection is for your organization.
Compliance Standards
Determine if you need to adhere to specific industry regulations.
Resource Availability
Consider your IT team’s capacity to manage infrastructure.
Operational Flexibility
Decide how important scalability and remote access are to your operations.
Make the
Right
Choice
Security Requirements
Assess how critical data protection is for your organization.
Compliance Standards
Determine if you need to adhere to specific industry regulations.
Resource Availability
Consider your IT team’s capacity to manage infrastructure.
Operational Flexibility
Decide how important scalability and remote access are to your operations.
Make the
Right
Choice
Security Requirements
Assess how critical data protection is for your organization.
Compliance Standards
Determine if you need to adhere to specific industry regulations.
Resource Availability
Consider your IT team’s capacity to manage infrastructure.
Operational Flexibility
Decide how important scalability and remote access are to your operations.
Understanding KanBo’s Installation Options
Scalability & Flexibility
KanBo scales efficiently to support 1,000+ daily users, adapting to growing enterprise needs with flexible resource allocation and performance optimization.
Compliance
Meets industry regulations and security standards across all deployment options, with specialized compliance for government (GCC High) and enterprise requirements.
Integration
Full control over data location, storage, and access policies. Choose between on-premises, cloud, or hybrid storage to meet sovereignty requirements.
Data Ownership
Seamless connectivity with Microsoft ecosystem (Teams, SharePoint, Office 365) and existing enterprise systems through standardized APIs and protocols.
Resource Planning
Adapt KanBo to specific organizational workflows with configurable interfaces, custom processes, and integration options across all deployment types.
Customization
Optimize IT resource allocation with flexible deployment options. Scale computing resources, storage, and user licenses based on organizational needs.
